How to Keep Your Online Meetings Secure

There are many choices and ways to connect individuals and groups through online video conferencing from older platforms like Skype to the now widely used Zoom.
And with our high-speed, reliable fiber internet, you can enjoy clear, consistent video and audio conferencing online with your family, friends, and co-workers, and even feel as if you are in the very same room together!
Yet, security risks exist for online video conferencing users. These risks can range from the unauthorized recording of video and audio conferences by outsiders to “Zoom Bombing,” where uninvited strangers can parachute into a seemingly private video conference and hijack it. Indeed, some incidents were so disturbing that the FBI felt the need to speak out and issued a public warning about the potential threats.
Fortunately, you can take steps to secure your online video conferences better. Read below to learn several ways to utilize this amazing technology safely and confidently.
Establishing a personal, unique Meeting ID code before each online video conference and a separate, carefully-shared password or PIN number is one of the simplest—and best—measures you can take to secure your meeting. Don’t overlook this most basic of protections!
Many online video conference apps offer a feature that allows the conference host to admit people to the “meeting room” from a “waiting room.” The waiting room enables the host to see who is trying to enter before they can actually join the conference, adding an extra level of security.
Allow “notifications” every time someone enters—or attempts to enter—the online video conference meeting room. This setting allows the conference room participants to see if any uninvited “guests” enter and try to create any mischief.
After you’ve set your unique meeting ID and password and safely admitted only invited participants into the conference, be sure to “lock the room.” This feature prevents anyone else from entering after you’ve locked the conference—and also encourages your guests to arrive on time for the meeting!
The best online video conference software developers regularly test their programs and apps for security compromises and flaws. Occasionally, they will update their software and create security patches. These updates and security fixes are only protective if you and your fellow online video conference participants install them! So be sure to look out for these updates and patches, or even allow automatic updates!
Online video conferencing is a fantastic technology that brings people closer together—and can make working groups more collaborative and productive. Taking the five steps described above will help keep your online video conferences safe and secure.
For more tips on how to safely navigate the web using DayStarr fiber internet, be sure to follow our social pages!
Disposing of Old Devices Safely
[1/11/2022]Now that you’ve gotten those fun new electronic gadgets for Christmas, you’ll need to dispose of your old ones. You can’t just toss them in the garbage and start fresh with the latest iPhone since they’re full of your photos, emails, banking information and other important information.
Luckily, you can safely get rid of your old cell phone, tablet, laptop or desktop computer, then start enjoying those new devices with our internet!
Back It Up
The first step is to back up your information. Backing up your data regularly — even when you’re not getting rid of your device — is a good habit to get into. Whether it’s music you’ve downloaded, documents you’ve typed or pics you’ve snapped, backing up is a form of insurance in case your computer ever crashes or gets hacked.
When discarding an old device, think about what you want to keep. Some people back up everything and sort through it later, and there’s nothing wrong with that! But if you’ve owned your device for a while, backing up every single file might be a lengthy endeavor. You might prefer to pick and choose what you save.
Either way, you have three options for backing up your device. Data migration is a techy-sounding term for when data gets moved from one location to another. In this case, we’re talking specifically about storage migration, when information is changing storage mediums.
Device to Device – Some devices, like desktop computers, will allow you to transfer data between devices. Using Migration Assistant for either Mac and Windows, you can even transfer between the two different systems – although the process can be a little tricky for the less tech-savvy.
External Storage – In this case, your external storage device will be the middleman. You start by transferring all your data to a separate device. Depending on how much data you have, your drive could be as small as a USB flash drive or as big as an external hard drive.
The Cloud – The cloud is the current favorite for data migration because it’s super easy and doesn’t require any extra hardware. This transfers all your data to the cloud via the internet. Once complete, your files can be accessed from any device. It’s fast, simple and secure, making it the optimal choice for data migration beginners.
Do a Final Cleanup
Before you toss your old device, be sure to log out of all your websites, wipe any saved passwords and unpair your devices. Finally, erase the computer’s hard drive. You’re washing your digital fingerprint from the device and protecting yourself in the process. Most computers and mobile devices can be restored to factory settings through built-in utilities.
Toss It Without Hurting the Environment
Because empty devices are filled with electronic components and substances like lead, mercury and cadmium, they’re hazardous material and shouldn’t go into a landfill. Take it to your local hazardous and electronic waste depot. If it still has some life in it, consider donating it to someone else who might enjoy it!
Now you’re set to enjoy your new gadgets! Don’t forget you’ll need great internet to get the most out of them. Call us today at 989-720-6000 to learn what’s available in your area.
DayStarr Christmas Party!

Each year we throw our DayStarr employee Christmas party to celebrate Christmas as a company, celebrate DayStarr’s achievements over the past year, give back to our employees, celebrate with family, and bond as a team. This year the party kicked off at noon with lunch, followed by a dessert competition, where employees brought in homemade baked goods and we all voted for our favorites. There was also a hot cocoa bar set up with all the goods.
The party continued with reindeer games for the kids including a multi-event relay race where the winners were given trophies. There was also an adult (employee) relay race which consisted of four teams representing four customers. If you followed along on Facebook you saw how our finalists were chosen and how Jan Krupp won three months of FREE service!!
There was also some work-related stuff as our Management Team shared their departmental year in review stats. The Management Team on behalf of the entire company also gifted Collin Rose, DayStarr President, an annual pass to Greenfield Village as a Christmas gift!
We recognized our employees for their achievements in our Core Values: Team Player, Passion, and Servant’s Heart. Our 11 nominees received a thank you card and a $20 Visa gift card. Nominees included: Dennis, Katie, Austin K., Luke, Blake, Avery, Austin S., Jared, Steve, Mark, and Brent. After a vote the week prior, we awarded our three Core Value Champions: Team Player Champion: Cameron Wilson, Champion of Passion: Dan Pray, and Servant’s Heart Champion: Mark Berndt.
After the games and presentation, everyone enjoyed the event activities including basketball, cornhole, fowling, knockerball, and dodgeball. It was an awesome afternoon full of fun and celebration of the incredible team we have here at DayStarr.
Employee Feature: Cody Vincent

“One of my favorite things about working for DayStarr is the team atmosphere. From day one, DayStarr has gone above and beyond and I have felt the support from every team member no matter what questions I’ve had,” stated Cody. “Also seeing the support, the team provides to customers is amazing. From the smallest of inquiries to an outage the team is all working together to help the customer.”
When Cody isn’t assisting our wonderful customers in the office, he enjoys spending time with family and friends. He also has a passion for cooking and photography. You may find him shooting at archery events around Michigan as well as giving back to the sport by instructing youth archery at the Shiawassee Conservation Club.
Cody was born and raised in Owosso, Michigan, and graduated from Owosso High School. He then went on to earn an associate degree in Business Management from Baker College.
Next time you’re in the office or call in, take a minute to welcome Cody to the DayStarr Team.
DayStarr January Price Change
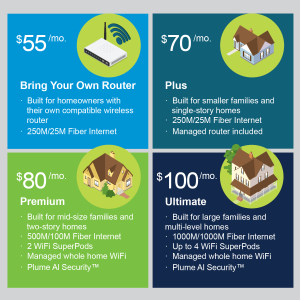
With the rising costs across many areas of our business–some more than doubling this year–we’ve made the tough decision to increase our internet prices. Our team has thoughtfully and carefully looked at our packages and arrived at the prices we believe are fair and competitive. We’ve also increased the upload speed on our two most popular packages: the “Bring-Your-Own” router and Internet Plus packages.
This change enables us to continue in our passion to deliver high-value products and provide the best customer experience. We are committed to hiring locally and doing everything we can to support the local economy.
We are committed to transparency, maintaining your trust and support, and improving lives in our communities through communications.
Customers who pay monthly will see this change on their January invoice. If you signed up after July 1 2021, your new rate will not take effect until July 1 2022. Customers who pay annually will automatically be rolled into the BYOR plan at the end of their year of paid service. Please let us know if you would prefer another plan option.
| JANUARY 2022 PRICE CHANGE | ||
| PACKAGE | Old Price | New Price |
| BYOR (NOW 250M/25M) | $50/mo. | $55/mo. |
| INTERNET PLUS | $60/mo. | $70/mo. |
| PREMIUM | $75/mo. | $80/mo. |
| ULTIMATE | $100/mo. | No Change |
Like always, if you have questions, concerns, or need help with your DayStarr account, please feel welcome to talk to our team via phone, email or chat from our homepage. We’re here to serve you!
How Fiber Internet is Different
[12/29/2021] Internet technology has advanced exponentially over the past three decades. Faster and more reliable than ever, today’s consumer has many choices when it comes to high-speed internet.
But if your neighborhood has a variety of options, which kind of internet technology should you choose? Is there any real difference between the different internet services available? And what exactly are these technologies anyway? And how do they work?
At DayStarr, we hear these questions all the time, and understand how confusing it can be.
We present this primer below to explain key terms and technology to help inform you and make better choices about the best internet service to suit your needs.
What is Coax Cable Internet?
Coax cable, short for coaxial cable, is the same technology used to provide “cable television.” It is composed of an insulated copper core of wires, which can carry both internet and television signal simultaneously.
As an “asymmetric” technology, cable’s primary disadvantage it’s markedly slower downloading speed. But, for the typical family and business user, cable’s downloading speed is probably sufficient. Cable has been a common technology for decades and many businesses and residential customers use it, especially since it can also provide television service.
What is Fiber Broadband Internet?
Fiber optic internet uses cables containing extremely thin, hair-width, glass-like “strings” of fiber material. Unlike coax cable, fiber optic technology converts internet data in the electrical signals into light, and then transports that converted light at extremely fast speeds into your modem and home. Because fiber optic technology transmutes data into light, it is much faster than coax cable internet.
Fiber optic internet can sometimes be more expensive than coax cable because the infrastructure isn’t available everywhere yet. Thus, establishing fiber optic internet service and connecting it to your home or business carries higher upfront costs than coax cable, which is prominent in most residential areas.
And what is Wireless Internet?
Wireless Internet is provided through “the air” rather than through wires or cables installed and connected to your home or building. Transmitted through a “Point of Presence” such as a transmitter radio—like on a “cell phone tower”—it doesn’t rely on substantial amounts of physical infrastructure like cable and fiber optic internet.
Wireless Internet is also “fixed”—the data transmitted to your home or business does not vary from the data plan with which you contract. If you choose a 25MBs per second speed plan, that is the speed your internet will be delivered. If you choose a 1GB per second speed plan (the fastest speed Wireless Internet currently offers), that’s what you’ll receive. But keep in that it is more expensive than coax cable, as well.
More common in rural areas (where there is less of a broadband infrastructure grid), Wireless Internet is provided by 3G and 4G cellular data service providers, such as cell phone service companies, as well as via satellite and “dishes.”
And don’t confuse “Wireless Internet Service” with “Wi-Fi!” They’re commonly confused and the names are easily interchanged with one another.
Remember that Wi-Fi refers to the router-based wireless-system in your house or business—internet enters your home through the modem and is transmitted through a Wi-Fi router to all of your Wi-Fi-capable devices. Wireless Internet, on the other hand, is another form of internet service, like fiber optic or coax cable service.
So which is best? Fiber or Cable or Wireless?
Call us biased, but Fiber Optic Cable is hands-down the fastest, most reliable and highest quality internet service technology available on the market today. The maximum transfer rates of fiber internet are higher than any other service available.
Fiber infrastructure is newer than cable or most Wireless infrastructure, and that improves performance and reliability.
Keep in mind that fiber may be a bit more expensive, at least at first. And perhaps you’d find the convenience of a single bill for both internet and cable appealing. Or you may live in a rural or more isolated area where wireless internet is your best—or only—option for high-speed internet service.
So be sure to do your homework. Research and ask questions. And when you’re ready, reach out to our helpful and knowledgeable team to let us assist you! We even reward you for referring a friend!!
5 Ways to Secure Your Personal Online Data
[12/29/2021] Is your personal online data safe from the growing security threats that, regrettably, are a part of our online world today? It’s a question every internet user needs to ask themselves.
Given the threats of phishing, ransomware, and other scams, it’s worth taking stock of your current online security and considering additional measures you can take to protect yourself.
Below are several tips to help you and your family better secure your online data and navigate the online waters more safely.
Antivirus software is an essential tool in your digital toolbox. It can help protect you and your family from threats that could steal your personal information, login credentials, and other sensitive data. Popular programs include McAfee Antivirus Plus, Norton Antivirus Plus, Bitdefender Antivirus Plus, and Kapersky Antivirus.
Most devices like computers, laptops, tablets, and smartphones come equipped with security features and privacy settings designed to protect users from digitally sharing personal details, such as your name, email address, and location while browsing online. Though none of these settings are totally foolproof by themselves, they can be a helpful first line of defense against many common threats. Be sure to review the privacy settings on each device and choose the level of protection with which you are most comfortable.
People naturally use social media to share details of their lives. From birthdays to anniversaries to new addresses, social media pages can be a treasure trove of personal information that can tip off hackers to passwords and security question answers. Think carefully about what information should and shouldn’t be shared—especially when filling out those seemingly innocuous “copy and paste” surveys. Talk to your family about posting wisely but not widely.
Let’s face it—when installing a new app or logging into certain e-commerce or other websites, it’s just easier and faster to login in with our Facebook or Google accounts, rather than reentering our personal details for the umpteenth time. But that means you need to be careful with the data and information Google and Facebook share with the other Apps. Be especially attentive to the “permissions” you grant Facebook and Google through their privacy settings, as they connect your accounts with these other Apps.
Although some of the programs listed in our first tip about Antivirus Software include them already, if you do not have them, consider installing Adblockers and Tracker Blockers. Ads are annoying, but they can also “take” some information from your devices that you would rather not share with an ad you didn’t want to see popup in the first place. Similarly, Trackers can “follow you” around the internet as you leave a trail of your online activity. Adblockers and Tracker Blockers can often be installed directly onto your web browser, and help provide protections against privacy exposures from ads and trackers, as well as reduce your overall privacy risk.
Finally, consider establishing a Virtual Private Network. Now, we know that sounds a bit technical, and maybe even scary. But VPNs can provide extra layers of protection and privacy on top of the other measures you’ve already taken above. A VPN moves your data through a “tunnel” to a separate, secure server first, and then encrypts your personal data before it “hits” the web, shielding and even hiding sensitive aspects of the data, such as your location, from potential threats. There are many VPN service providers, including NordVPN, ProtonVPN, CyberGhost, ExpressVPN, and SurfShark. Another option, TunnelBear, is a less edgy, more user-friendly option for first-time VPN users.
The tips above are a good start to protecting your privacy and online data. And by employing these and other safeguards, you can use DayStarr, fast fiber internet from confidently, as well as reliably!
When Cyberbullies Strike: How to Support Your Child
[12/2/2021] Kids of every generation have had to endure bullying and all manner of meanness, even outright intimidation and threats. Sadly, the internet has only exacerbated the problem.
When once a bullied child could escape its effects by simply leaving the playground or schoolyard, bullying now follows kids home digitally. From a laptop to their smart phone, kids can literally take cyberbullying with them wherever their devices are. In today’s digitally-dominated world, it can feel like there is simply no escape from its impacts.
It’s no wonder that so many children are experiencing serious emotional, even psychological harm, from cyberbullying. The good news for parents is that there are concrete steps they can take to help their kids navigate and mitigate this unfortunate part of their growing-up.
What You Can Do
Fortunately, there are steps you can take to reduce cyberbullying and help your child deal with its fallout.
You know your kids and can often sense their emotions, so trust your instincts when you think something may be wrong. Perhaps they seem less enthusiastic about activities they typically enjoy, or are suddenly quieter than usual. You may notice signs of lack of sleep, or that they’re complaining of more frequent headaches or stomach issues. Try to notice a pattern in changes in mood and demeanor after they’ve been using their digital devices.
Reach out to them and ask them to share what may be happening, taking care to do so as gently and warmly as possible. Often kids feel that their parents may be unhappy with their “overuse” of digital devices and become defensive, so try to be mindful of avoiding an accusatory tone in order to encourage disclosure and open-dialogue.
Once you’ve identified the source of the cyberbullying, do not forget to document it! Screenshots of the offensive messages can serve as key evidence later when dealing more directly with the problem.
In response to this pervasive problem, many apps have reporting mechanisms to remove the offensive content and even suspend or ban offenders. You can also “block” the cyberbully from viewing and interacting with your child’s social media page. If the cyberbullying is happening at school, learn your school’s reporting requirements and use its resources to safely and appropriately confront the problem.
Practice empathy and understanding, without minimizing the very real pain your child may be experiencing. Gently remind them that these problems pass with time, and so does the pain. And take the time to post supportive comments on their pages, and encourage other positive friends, peers and family-members to post favorable comments, too. That can serve to drown out negativity and even drive bullies away.
The internet is also a source of great connectivity that can bring people together to learn and share, so don’t forget its countless benefits, too.
Be sure to follow our social pages (Facebook, Instagram) for more tips and advice on navigating the internet safely and productively.
How to Prepare for (and Ace!) Your Next Virtual Job Interview
[11/22/2021] Virtual interviewing is becoming more and more common in today’s job market. While remote interviewing may be more convenient, the distance and technical difficulties can be awkward, or even jarring, to would-be applicants.
Fortunately there are tips from interviewing experts that prospective job seekers can use to get through—and even nail—a virtual job interview. We share some of their key insights and recommendations below.
The Interview Environment: Organize and Professionalize Your Space
You already know you should “dress for success” and make sure that you look your polished best for an interview. But when you’re interviewing from your home, the interview space and background could be distracting, even off-putting, to potential employers. Take the time to make your space look its best, too.
Clean and Declutter: This seems obvious, but make sure you take the time to de-clutter your surroundings, whether it is your bedroom or home office desk. Show your would-be bosses that you quite literally have it together at home, which will make a better impression of being grounded and composed.
Lighting: Proper lighting is a detail too-often overlooked. Be sure to “light yourself” from the front, and not from the back! The latter can create a rather eerie, even sinister visage. Where possible, aim for “cool light,” which is whiter in color, rather than “warm light,” which is yellower. These seemingly small details help put your best foot forward.
Interviewing Skills and Tips
There are countless tips on interviewing available online, but we share a few below that are particularly relevant to remote interviewing.
Keep Any Notes Short and (Mostly) Out of the Way
Like in any interview, try to not over-rely on notes. It is easy to get flustered and lose your place in notes, so keep them sparse and well-organized. Index cards placed outside the viewing area may be especially helpful, with key information and points printed largely and visible to you, but out of sight from the interviewers.
Keep Eye Contact—And Look Into the Camera, Not at Your “Mirrored Image”
Another common mistake is the awkward “stare” that people make when they forget to look into the camera, and instead watch their own reflected image while using the app. You will look less engaged, and even odd, at least compared to applicants that remembered to look “correctly” at the camera.
Watch Your Speaking Pace
Avoid speaking too quickly, a common giveaway of nervousness. Practice and rehearse answers to likely questions, and actually time how quickly you are speaking.
An Interview is a Conversation
Ultimately, an interview is just another conversation. A back-and-forth discussion makes for a much better interview, so be sure to have researched the job thoroughly and come prepared with questions. Look engaged when the interviewer is speaking by maintaining eye contact (see above about looking into the webcam!) and nodding your head occasionally. Don’t miss an opportunity to add something of value to what the interviewer says.
Get Internet You Can Rely On
One last tip: Make sure you have high-speed internet with fast download and upload speeds that you can rely on for a steady connection throughout your interview. (Adequate upload speeds ensure your video is clear for the interviewer on the other side of the virtual table.)
With DayStarr Fiber Internet, you can video call without fear of a dropped connection or glitchy experience, so you can tackle your interview with confidence.
Do You Need a “Digital Will?”
[11/16/2021] You’ve set up a living will, established an estate plan, divvied up the family heirlooms, and even made provision for your dog—but have you created a Digital Will?
Chances are, you haven’t even thought about what happens to all of your digital assets—your online photos, social media sites, email accounts, etc—after you’ve died. However, it’s something you probably should consider.
What is a Digital Will?
Quite simply, a Digital Will is a document of instructions to another person (the Digital Will Executor) on how to allocate and/or dispose of your digital assets. This includes granting the Digital Will Executor access to your digital assets, and setting parameters for controlling who can and cannot access them.
Do I Really Need a Digital Will?
You might—or at least you may be glad you had one (and so will your loved ones). Think about your online presence accumulated over the years—all of the digital assets you have like your online photo albums, music, documents, email accounts, social media accounts, online banking, etc—and that unlike your home and other physical property, which can be distributed “the old-fashioned way,” login credentials, tech company privacy policies, and the law can often slow-down or even prevent easy access and reallocation.
Ask yourself if is it “okay” for tech companies to just delete your digital assets for all time after a several years (and often just months) of non-use. Alternatively, ask yourself if you want your online presence to remain online, and even public, forever? Or would you prefer that decisions about these assets will be controlled by someone you trust?
A Digital Will can help resolve these issues in a way you are comfortable with, and facilitate a smooth transition.
What Should I Include in My Digital Will?
Unlike normal wills, you probably don’t need a formal Digital Will drafted by an attorney (although people with more extensive digital presences may want to consider consulting an experienced lawyer).
Below are the basic components and steps of creating a Digital Will:
Write a list of every online account you have, from email accounts, to social media sites, to photo-sharing sites. Think broadly, and go back to sites you haven’t used in a while, like, for example, that online blog you created that summer. And don’t forget about sites that have your credit card or bank account information—especially those that utilize the auto-pay feature!
It goes without saying, but you should pick someone you trust and who will be discreet—and someone that others are likely to trust after you’re gone, too. Choosing an alternative executor is also a good idea. Be sure to name the person in the Digital Will itself and provide contact information.
This is where you need to think hard about who-gets-to-see-what. Perhaps you only want your photo albums from your Facebook page to be accessible—but perhaps viewable only to friends. Perhaps you’ve decided that your Youtube videos from decades ago should never see the light of day. Set your boundaries and write them as specifically as possible.
Gather all of your login credentials and passwords so your Digital Will Executor can access and control them. Consider a password locker to better secure them in one place.
Once completed, choose a safe place to keep your Digital Will. Perhaps it can be kept with your will and other important documents. You may even want to keep it in a safe deposit box at a bank.